>> 목록보이기
#Kali Linux
#칼리리눅스
#nmap
#포트스캔
#Port Scan
#nikto
#웹 서비스 기본설정 점검
#zaproxy
#owasp-zap
#웹어플리케이션 취약점 점검
#공개용 취약점점검 도구
웹해킹 훈련장(172.16.15.116:40080)에 대한 공개용 도구기반 취약점 점검
실습순서 요약
- Google 등의 웹 검색 엔진을 이용한 웹 서비스 탐색(비공개 서버이므로 여기서는 생략)
site:www.target.co.kr admin login(관리자 페이지 탐색)site:www.target.co.kr download(파일 다운로드 기능 탐색)site:www.target.co.kr 글쓰기(게시판 글쓰기 기능 탐색)...- Nmap 간략 스캔:
sudo nmap -p- -v 172.16.15.116 - Nmap 상세 스캔:
sudo nmap -p 22, 80, 111, 139, 445, 3389, 6566, 8200, 9091, 10080, 39507, 40080, 43389, 51413 -A -v 172.16.15.116(-p 다음의 포트 목록은 공백이 없어야함) - Nikto 스캔:
nikto -port 40080 -host 172.16.15.116 - OWASP-ZAP 스캐너:
zaproxy(Automated Scan의URL to attack:에 "http://172.16.15.116:40080" 입력하고공격!) - Nmap-Nikto-Zaproxy 점검 결과 총괄:
00-172.16.15.116-40080-20200508.txt
점검대상 웹서버의 포트 스캔(Port Scan): 간략 스캔
sudo nmap -p- -v 172.16.15.116 -oN 172.16.15.116-nmap-in-brief-all.txt
sudo:nmap은root권한으로 실행해야 점검시간을 줄일 수 있다.nmap: 가장 일반적인 포트 기반 네트워크 점검 도구-p-: 운영체제의 모든 포트( 65536개)를 대상으로 점검 - 지정하지 않으면 Nmap이 선정한 기본 1000개의 포트 대상으로 개방여부 점검-v: 상태표시(verbose mode) -nmap점검은 시간이 많이 걸리는 데-v를 지정하지 않으면 많이 답답함.-vv를 사용하면 좀 더 장황하게 스캔 상태를 알려줌.-oN: 출력 파일은 평문으로 한다. 확장자는.txt여야 함172.16.15.116-nmap-in-brief-all.txt: IP주소 또는 호스트 이름, nmap 결과, 내부(in)에서 스캔, 모든 포트(all) 대상 개방여부(brief) 점검의 의미
kali@kali:~$ sudo nmap -p- -v 172.16.15.116 -oN 172.16.15.116-nmap-in-brief-all.txt
Starting Nmap 7.70 ( https://nmap.org ) at 2020-05-07 11:23 KST
Initiating Parallel DNS resolution of 1 host. at 11:23
Completed Parallel DNS resolution of 1 host. at 11:23, 0.01s elapsed
Initiating SYN Stealth Scan at 11:23
Scanning 172.16.15.116 [65535 ports]
Discovered open port 139/tcp on 172.16.15.116
Discovered open port 3389/tcp on 172.16.15.116
Discovered open port 22/tcp on 172.16.15.116
Discovered open port 111/tcp on 172.16.15.116
Discovered open port 80/tcp on 172.16.15.116
Discovered open port 445/tcp on 172.16.15.116
Discovered open port 39507/tcp on 172.16.15.116
Discovered open port 8200/tcp on 172.16.15.116
Discovered open port 40080/tcp on 172.16.15.116
Discovered open port 6566/tcp on 172.16.15.116
Discovered open port 51413/tcp on 172.16.15.116
Discovered open port 10080/tcp on 172.16.15.116
Discovered open port 43389/tcp on 172.16.15.116
Discovered open port 9091/tcp on 172.16.15.116
Completed SYN Stealth Scan at 11:23, 8.70s elapsed (65535 total ports)
Nmap scan report for 172.16.15.116
Host is up (0.000015s latency).
Not shown: 65521 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3389/tcp open ms-wbt-server
6566/tcp open sane-port
8200/tcp open trivnet1
9091/tcp open xmltec-xmlmail
10080/tcp open amanda
39507/tcp open unknown
40080/tcp open unknown
43389/tcp open unknown
51413/tcp open unknown
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 8.85 seconds
Raw packets sent: 65580 (2.886MB) | Rcvd: 131174 (5.509MB)
kali@kali:~$
웹 서버를 대상으로 하는 해킹은 대개의 경우 자동화된 기계적 공격이다. 기계적인 해킹은 거의 대부분 특정 포트를 중심으로 IP주소를 횡적으로 스캔하는 방식으로 이루어진다 (예: XorDDOS.Botnet의 22/tcp (ssh) root 비밀번호 스캔; WordPress 대상의 80/tcp 및 443/tcp 포트 스캔; 8080/tcp 포트 대상 취약한 Apache Tomcat 관리자 비밀번호 공격 등). 반면, 다양한 기계적 공격이 가능할 수 있는 취약점을 찾기 위해서, 홈페이지 취약점점검은 특정 웹서버의 IP주소를 중심으로 서버의 포트를 종적으로 스캔하는 방식으로 수행한다.
점검대상 웹서버의 포트 스캔(Port Scan): 상세 스캔
sudo nmap -p22,80,...,51413 -A -v 172.16.15.116 -oN 172.16.15.116-nmap-in-detail-all.txt
sudo: 가능하다면nmap은root권한 실행nmap:nmap명령어-p22,80,...,51413: 위의brief-all에서 발견된 포트 대상으로 점검 진행-A: 운영체제 탐지, 버전 탐지, NSE 스크립트 스캔,traceroute등 포트 대상의 거의 모든 점검을 수행-v: 상태표시(verbose mode) - 답답함 해소용 ^^-oN: 출력 파일은 평문172.16.15.116-nmap-in-detail-all.txt: IP주소 또는 호스트 이름, nmap 결과, 내부(in)에서 스캔, 앞서 탐지된 모든 포트(all) 대상 상세 점검(detail)의 의미
kali@kali:~$ sudo nmap -p22,80,111,139,445,3389,6566,8200,9091,10080,39507,40080,43389,51413 -A -v 172.16.15.116 -oN 172.16.15.116-nmap-in-detail-all.txt
Starting Nmap 7.70 ( https://nmap.org ) at 2020-05-07 11:27 KST
NSE: Loaded 148 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 11:27
Completed NSE at 11:27, 0.00s elapsed
Initiating NSE at 11:27
Completed NSE at 11:27, 0.00s elapsed
Initiating Parallel DNS resolution of 1 host. at 11:27
Completed Parallel DNS resolution of 1 host. at 11:27, 0.01s elapsed
Initiating SYN Stealth Scan at 11:27
Scanning 172.16.15.116 [14 ports]
Discovered open port 22/tcp on 172.16.15.116
Discovered open port 80/tcp on 172.16.15.116
Discovered open port 111/tcp on 172.16.15.116
Discovered open port 445/tcp on 172.16.15.116
Discovered open port 3389/tcp on 172.16.15.116
Discovered open port 139/tcp on 172.16.15.116
Discovered open port 43389/tcp on 172.16.15.116
Discovered open port 40080/tcp on 172.16.15.116
Discovered open port 6566/tcp on 172.16.15.116
Discovered open port 9091/tcp on 172.16.15.116
Discovered open port 39507/tcp on 172.16.15.116
Discovered open port 10080/tcp on 172.16.15.116
Discovered open port 51413/tcp on 172.16.15.116
Discovered open port 8200/tcp on 172.16.15.116
Completed SYN Stealth Scan at 11:27, 0.42s elapsed (14 total ports)
Initiating Service scan at 11:27
Scanning 14 services on 172.16.15.116
Completed Service scan at 11:30, 151.09s elapsed (14 services on 1 host)
Initiating OS detection (try #1) against 172.16.15.116
NSE: Script scanning 172.16.15.116.
Initiating NSE at 11:30
Completed NSE at 11:31, 60.61s elapsed
Initiating NSE at 11:31
Completed NSE at 11:31, 1.02s elapsed
Nmap scan report for 172.16.15.116
Host is up (0.000043s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 66:fa:54:c4:e9:92:c8:7c:0c:e5:00:e9:e2:e2:4b:b2 (RSA)
| 256 72:da:a7:18:ef:b6:99:a8:f5:66:2c:cf:63:2e:cb:3c (ECDSA)
|_ 256 85:0a:c2:d9:62:ba:ce:53:b7:68:1c:d3:14:04:72:df (ED25519)
80/tcp open http Apache httpd 2.4.38
| http-ls: Volume /
| SIZE TIME FILENAME
| 8.9G 2020-02-21 08:54 Windows%2010%20AP-GS.ova
|_
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Index of /
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100024 1 39507/tcp status
|_ 100024 1 44884/udp status
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.9.5-Debian (workgroup: WORKGROUP)
3389/tcp open ms-wbt-server xrdp
6566/tcp open tcpwrapped
8200/tcp open upnp MiniDLNA 1.2.1 (OS: Debian; DLNADOC 1.50; UPnP 1.0)
9091/tcp open http Transmission BitTorrent management httpd (unauthorized)
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Transmission
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-server-header: Transmission
|_http-title: Site doesn't have a title (text/html; charset=ISO-8859-1).
10080/tcp open http Apache httpd
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-favicon: Unknown favicon MD5: 69C728902A3F1DF75CF9EAC73BD55556
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Apache
| http-title: Login :: Damn Vulnerable Web Application (DVWA) v1.9
|_Requested resource was login.php
39507/tcp open status 1 (RPC #100024)
40080/tcp open http Apache httpd 2.4.41 ((Win64) PHP/7.4.2)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 1 disallowed entry
|_/admin/
|_http-server-header: Apache/2.4.41 (Win64) PHP/7.4.2
|_http-title: \xEC\xB7\xA8\xEC\x95\xBD\xED\x95\x9C \xEB\x88\x84\xEB\xA6\xAC\xEC\xA7\x91\xEC\x97\x90 \xEC\x98\xA4\xEC\x8B\xA0 \xEA\xB2\x83\xEC\x9D\x84 \xED\x99\x98\xEC\x98\x81\xED\x95\xA9\xEB\x8B\x88\xEB\x8B\xA4! - \xEC\xB7\xA8\xEC\x95\xBD...
43389/tcp open ssl/unknown
| ssl-cert: Subject: commonName=DESKTOP-FV4LV36
| Issuer: commonName=DESKTOP-FV4LV36
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-02-17T00:34:35
| Not valid after: 2020-08-18T00:34:35
| MD5: c9c1 6f55 090c 53e5 62d9 c9f0 691c 2e20
|_SHA-1: bced db31 0670 0497 c803 d1bd 23cc a932 ff2a 0862
|_ssl-date: 2020-05-07T02:30:12+00:00; 0s from scanner time.
51413/tcp open unknown
| fingerprint-strings:
| Kerberos:
| w\x9b{
| SMBProgNeg:
| (2g?
| 1LVz@
| oe'|n
| L@W|
| \xd5E
| TLSSessionReq:
| 2ylr
| CK~wZA
| 9\xa7]
| 4}"CqY
| QnDo
|_ .T7X
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port51413-TCP:V=7.70%I=7%D=5/7%Time=5EB37255%P=x86_64-pc-linux-gnu%r(TL
SF:SSessionReq,205,"Wk\?\xba\xba\x8d\x13%%S\x06=5\x8f\xb3\x81\t\x8a\x1d\x1
SF:7\xd4\xa8\x8f\xb5\xff\x15d`\x01Fu\xcb\xa8\xd0\t\?\x10\x05\xd3`\x15\x18\
SF:x82\xf7\xe5\r\xad\x08K\xd6\x06r\x9c_/\xf4\xafQ\x90\xc2m\xe0\?\xfc\xe73\
SF:xe4V\x86\x8f\x89\x9bI!q\xee\x01A\xff\x08\x88\xea2\x19\xd6\x82\x1c\x1d\x
SF:f2\x0c\xa7\*\xcf\x90\x12\xeb\x9b\x95\.-\x9c}C>\xbe\xcd\x12N\xfd\xe4\xc5
SF:\xdc\xc5\x0b\x14\r\x0f\x9c\xfd\xe1\x1c\x86XA9\x8e\x942ylr\x9a\xf7\xa0\x
SF:e7\xde\x9c,\x99\x07/&\x17\xf3a\xa4\)w\x11\x01\xf0\x01\xbf\x89\x81\xc4\x
SF:f0H}\xba\x01\xcc\xd7\r\xd4U\xd00\x948e\xf8\xf9\xa2\xf90\xc2\xa0\xe3\x97
SF:Vv\xd88\xd6\x8f\x85\xac\xc4\x7f\xd3\xbe\x1a\x13P\x8fY\x17j\(\xcb\x88\$C
SF:\x8c\t4l\x07M2\xa7\xc9\xffU\xf3\x81\xb3CK~wZA\xea',\x8e\xb9\0\x1bS\xac\
SF:x99a\xae\xcb#\x8d\)\xd6\xa0\xea\x19\x97C\x05\x82\xff\x93\x88\x0b\x88\x1
SF:8\xbb=\x06K\tp\x8c\x15\xd7\x1d9\\\xa7\]\xbc\xaf\xc0\xf7\xd3#\xaf\x80\xd
SF:79\xc0\xc1\n\xdb\xde\|\x19\x08z\xb2:\xa3\x7f\xcd\x03\xd2\xda2\xdbQ\xff~
SF:Ys\xbb\xe0\xae00\x1bBkW\xdb\xb3\xbdgG7\x06\x82\x1a\xdd\xb9\xef\.\xa3\x8
SF:3\.\?o\xc0FUL\x05\xfa\xa4\xfa\x13\+\xf6\x9c\x7f6d\xa9s\x90h\xea\xfe\(\x
SF:a8\xde\x80_,_\x84Nd\tw\x1f\x02\x1b\xed4}\"CqY\x01:\x97\xd2R\$\xd5`w\x1b
SF:\xe8jX\xe2\xc2u\r\x0b\xd91\xcc\+\xe7\xd2ie\xae\xbc\x9dV\xbe\xde\xce\xf6
SF:\xeeP\xb5\x13\]\x94\xe8\x9cl\x13\xaa\x7f\xcf\x03O\x85\x958\xdd\xee\xe6\
SF:xc1\xbb\xb6y\x06\xf3\xa3\x1d\xb9\x9d\x1c\x10M\x9e3\x88\x053\xec\$\x18l\
SF:xaewU\xd7\x93\+w\xf3gOS\0QnDo\x834\xaa\.T7X\xde9{\xddY\x11tk\xf2\xb68\x
SF:9b&\r\$F\x14:\x1d%\x07\x17i=\xb0x\x16\xe4\xad\xc4\$\x9c\xd0\x93}`\x84\$
SF:\xc0\x1f\xa9-\x17g\xfb")%r(Kerberos,72,"\xf7\xde\x1f\x1c\^C\xf7l\xcb\xa
SF:7%\x9f\x0e\xe8\xe6\xed\x92\na\x82x\xb9\x20-\xcf\xcc\xc4w\\\x9b{\xf0%I\x86\xf6J\t\xc3\xc
SF:4\x8a\xca\xec\x11\)\x8bS1\xb2\xc9\0e\x1a\xa4g\\7\x90\xb4\x0b\x90l\xbe\x
SF:a6&\xf8\x1f\x08b\xe5\x01@\xaae}\x83\xd2C\xd3_>\xf3\x1b\x06\x10\xa2N\xc0
SF:\xf4\x8e65J\x1d=\xa0\x1b\x8e\['\xea\xc3I\.\xb2\xc6\xd3=\xc7\xc9N\xc8\xb
SF:e=R\xd9\xcb\xd9\x96\x9b\xa9\xbd\x914\x12\x89\xcf\xa1xe\x0c_\x05{\xebX\x
SF:ack\xe4\xd1\.\xf8:\xa8\|j\x0fM\xa0\x0b\0\xd8\xfa\x8a\xde\$\xd0-\x9a\xa4
SF:\xdbw\x8e\(2g\?\x13N\xa9m\xd9\x13@\xec\x13\x9f\xf9\t\xea\xaa\x81\xa7\x1
SF:3\xc8N\[G\x1f\x08\x91\xc0\x02\x0e\x11\xf0P\xee\xe1\xddg\xfd~~\x86,\xe8\
SF:x13\x1a\xd3\xb1\xda\x93\xa8\xe7I\xce\x84\x81\x88BCO\xcd\x05\n\x12\x17\x
SF:f3\xca\[\x96\xdb9C\xe8\x8bL{\x04\x02\xf2\xb5\x95\xc1\x06#\x06Q\xe6\xa8g
SF:\xbe\x0c\x04HC\xa2D_\x90n\xd9\+\x15p\x15\n}\xea\xdd\x1f\x880\x89\x20J\x
SF:0b\xff\xbf,\xac\xb5\x0ff6\x06\xff\x86\x9e\xbb\x16\xcdn\xe9C\xf0\xf1-\xa
SF:eW4\xf8R\x7f\x86\x028\xf8\x01\xbeC\x19D9\x9f\x9b1LVz@\x8aK\x16Ph\x18\x0
SF:fr9/\xa2\x9e\+\xdaoe'\|n\x9a!w\x0b\xc3\xad\|\xd0\x95\x8e\xfc\xe6\xe2\x8
SF:7A\xfa\xe3Ky\xc2\x1e\xbc\xae\x9bw9\xff}\xd3\xcf\xe2\x94\x97\xe4\xa1\xd8
SF:\xe4&\xe5>\x19\x1a\.\xe0\x11\xc0\x0f}\0\xa4\x91v\xd6\xcc\x12\xd6f@\xe2\
SF:xee\xce\xce\x0f\xa1\x05\xf9\xd4\xfb\xa1<\xe2\x92\+A\xe0bP\xac\xe6L@W\|\
SF:x0c\xce\x18\xd4\xf4\xc2%\xa3'\x16\xb0a\xbfT\x89\xfcX\x93\x01'\x16C\xc5,
SF:\x1aj\x1a\xd9\xf8\.\xfd\"\xb7TS=\xc4\xa9d4w\xf2\xbcu\x085\xbc1\xd2\xf8Q
SF:\x02A>A\x1eC\xd7\\\xd5E\xe0I\x85\x0em\0\x10{");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X
OS CPE: cpe:/o:linux:linux_kernel:3
OS details: Linux 3.7 - 3.10
Uptime guess: 16.046 days (since Tue Apr 21 10:24:47 2020)
Network Distance: 0 hops
TCP Sequence Prediction: Difficulty=252 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: Hosts: 127.0.0.1, MXLNX; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -2h15m00s, deviation: 4h30m00s, median: 0s
| nbstat: NetBIOS name: MXLNX, NetBIOS user: , NetBIOS MAC: (unknown)
| Names:
| MXLNX<00> Flags:
| MXLNX<03> Flags:
| MXLNX<20> Flags:
| WORKGROUP<00> Flags:
|_ WORKGROUP<1e> Flags:
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.9.5-Debian)
| Computer name: mxlnx
| NetBIOS computer name: MXLNX\x00
| Domain name: \x00
| FQDN: mxlnx
|_ System time: 2020-05-07T11:30:12+09:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-05-07 11:30:13
|_ start_date: N/A
NSE: Script Post-scanning.
Initiating NSE at 11:31
Completed NSE at 11:31, 0.00s elapsed
Initiating NSE at 11:31
Completed NSE at 11:31, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 216.71 seconds
Raw packets sent: 68 (5.696KB) | Rcvd: 153 (10.528KB)
kali@kali:~$
여기서 보여주는 nmap 결과는 서버 내부에서 자체적으로 실행한 것이므로
방해없이 결과를 얻은 것이다.
아마도 외부에서 nmap을 실행하면 이와 다른 결과를 얻을 수도 있다.
65536개의 모든 포트에 대해서 스캔을 하는 것은 매우 많은 시간이 걸리므로
실제 웹취약점 점검에서는 WAF/IPS에 예외 조치를 취한 후 간략스캔과 상세스캔을 묶어서
sudo nmap -A -v 점검대상_웹서버_호스트명으로
진행한다(이 경우에는 주요 1000개 포트만을 대상으로 한다).
Nikto 스캔
nikto -port 40080 -host 172.16.15.116 -o 172.16.15.116-nikto-40080-in.txt
nikto: 웹서버 설정 취약점 점검 도구-port 40080: 웹 서비스가 제공되는 포트 (여기서는 40080 포트). 기본은 80이다. (-ssl을 지정하면 자동으로 443/tcp 포트를 점검)-host 172.16.15.116: 점검 대상 서버 이름. 여기서는 호스트명이 없어서 IP주소를 지정함-o 172.16.15.116-nikto-40080-in.txt: 점검 결과 파일. 호스트이름(IP주소), 점검도구, 포트, 내부(in)로 꼬리표 붙임
kali@kali:~$ nikto -port 40080 -host 172.16.15.116 -o 172.16.15.116-nikto-40080-in.txt - Nikto v2.1.5 --------------------------------------------------------------------------- + Target IP: 172.16.15.116 + Target Hostname: 172.16.15.116 + Target Port: 40080 + Start Time: 2020-05-07 15:45:52 (GMT9) --------------------------------------------------------------------------- + Server: Apache/2.4.41 (Win64) PHP/7.4.2 + Retrieved x-powered-by header: PHP/7.4.2 + The anti-clickjacking X-Frame-Options header is not present. + Server leaks inodes via ETags, header found with file /robots.txt, fields: 0x20 0x59eb27067bd57 + Uncommon header 'x-frame-options' found, with contents: SAMEORIGIN + File/dir '/admin/' in robots.txt returned a non-forbidden or redirect HTTP code (200) + "robots.txt" contains 1 entry which should be manually viewed. + DEBUG HTTP verb may show server debugging information. See http://msdn.microsoft.com/en-us/library/e8z01xdh%28VS.80%29.aspx for details. + OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST + OSVDB-3092: /sitemap.xml: This gives a nice listing of the site content. + OSVDB-3092: /admin/: This might be interesting... + OSVDB-3268: /data/: Directory indexing found. + OSVDB-3092: /data/: This might be interesting... + OSVDB-3092: /README.TXT: This might be interesting... + OSVDB-3092: /readme.txt: This might be interesting... + OSVDB-3093: /admin/index.php: This might be interesting... has been seen in web logs from an unknown scanner. + OSVDB-3233: /test.php: PHP is installed, and a test script which runs phpinfo() was found. This gives a lot of system information. + OSVDB-3092: /LICENSE.txt: License file found may identify site software. + OSVDB-3092: /Admin/: This might be interesting... + OSVDB-3092: /license.txt: License file found may identify site software. + OSVDB-3092: /LICENSE.TXT: License file found may identify site software. + OSVDB-3092: /test.php: This might be interesting... + 6544 items checked: 0 error(s) and 21 item(s) reported on remote host + End Time: 2020-05-07 15:46:17 (GMT9) (25 seconds) --------------------------------------------------------------------------- + 1 host(s) tested kali@kali:~$
OWASP-ZAP 스캐너
zaproxy (Automated Scan의 URL to attack:에 "http://172.16.15.116:40080" 입력하고 공격!))
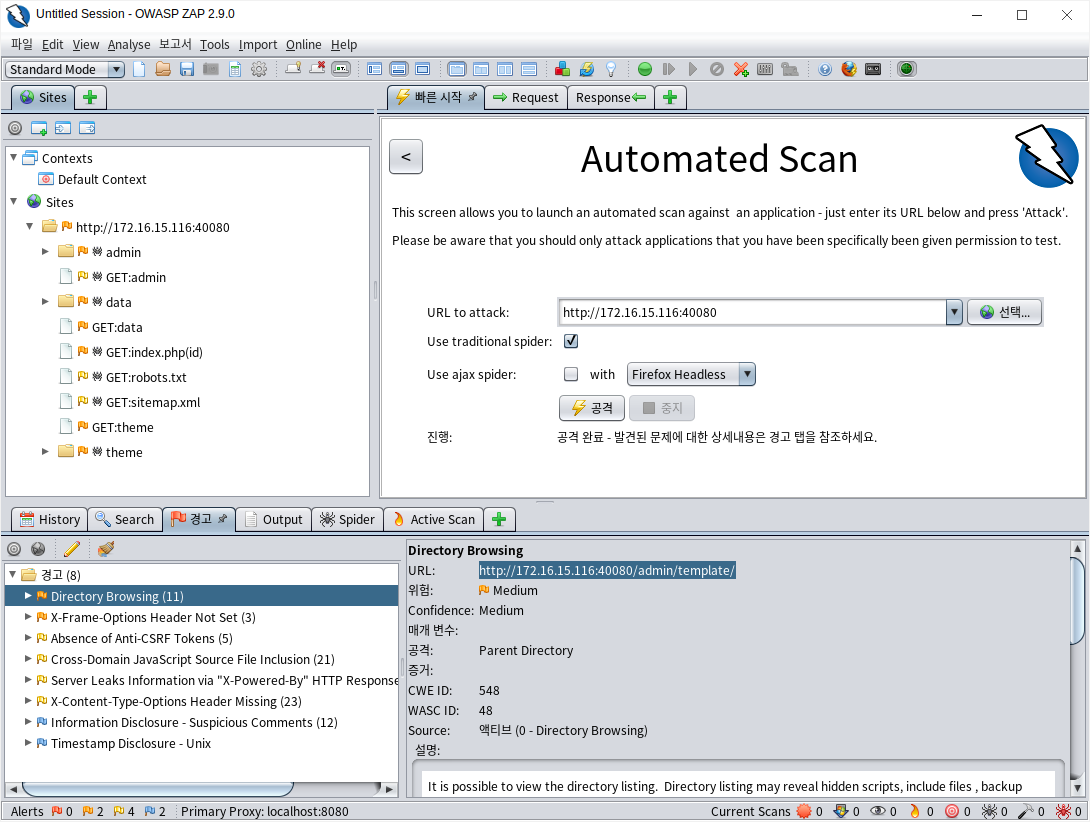
• OWASP-ZAP 취약점 스캐너로 172.16.15.116의 40080 포트 대상 취약점 점검 결과
Zaproxy의 점검 결과는 파일 -> Persist Session...에서 저장해 놓을 수 있다.
여기서는 172.16.15.116-zaproxy-40080-in으로 저장하였다.
다음 절에서 보겠지만 이 세션의 크기는 매우 크기 떄문에 - 실제 상황에서는 수 ~ 수십 기가바이트 -
가상머신으로 설치한 칼리리눅스의 저장공간을 모두 소진할 수 있으므로 주의해야 한다.
개인적으로는 OWASP-ZAP 스캔이 완료되면 스캔 결과를 취합하고 나서 별도의
세션으로는 저장하지 않고 버리는 편이다.
도구를 이용한 스캔 결과 취합하기
kali@kali:~$ ls -1 172.16.15.116-*
4 172.16.15.116-nikto-40080-in.txt
4 172.16.15.116-nmap-in-brief-all.txt
12 172.16.15.116-nmap-in-detail-all.txt
4 172.16.15.116-zaproxy-40080-in.session
20 172.16.15.116-zaproxy-40080-in.session.backup
65536 172.16.15.116-zaproxy-40080-in.session.data
4 172.16.15.116-zaproxy-40080-in.session.lck
4 172.16.15.116-zaproxy-40080-in.session.log
4 172.16.15.116-zaproxy-40080-in.session.properties
8 172.16.15.116-zaproxy-40080-in.session.script
kali@kali:~$
Nmap, Nikto, OWASP-ZAP 점검 결과 파일은 위와 같다. 다른 파일에 비해서 Zaproxy의 세션 데이타가 매우 큰 것을 볼 수 있다. 이 훈련장이 매우 간단한 누리집이어서 65kb 정도 밖에 되지 않지만 실제 서비스에서는 수~수십 기가바이트에 달할 수 있다. Kali의 디스크를 30GB로 만들었을 때, 현장에서 점검을 진행하면서 Zaproxy 스캔만으로 디스크가 모자란 경험이 있다. 이 때부터 디스크를 60GB로 설정하여 쓰고 있는 데 아직까지는 실제 점검에서 저장공간이 꽉 찬 적은 없다.
점검 결과를 취합할 파일의 이름은
00-172.16.15.116-40080-20200508.txt로 하였다.
00: 파일 목록의 가장 처음에 나타나도록 정한 문자열172.16.15.116-40080: 점검대상 호스트 이름 - 포트20200508: 취합한 날짜
지금까지 결과를 취합하여 정리하면 다음과 같다.
- 관리자 페이지 노출 취약점
:40080/admin/(탐지도구: nmap, nikto, zaproxy)
ACL 기반의 접근제어정책 미적용. 누구나 접근하여 ID/PW를 아는 경우에는 관리기능에 접근할 수 있음- 디렉토리 나열 취약점
:80/(탐지도구: nmap):40080/data/(탐지도구: nikto, zaproxy)
숨겨져 있어야 할 파일목록 노출로 추가 공격에 도움을 줄 수 있음- 시스템 관리 취약점
- 불필요한 포트 개방 (탐지도구: nmap) - 웹 서비스에 불필요한 포트는 접속을 차단해야 함
22/tcp: SSH 접속을 허용80/tcp: 디렉토리 나열 취약점이 존재하는 불필요한 웹 서비스? (8.9G 2020-02-21 08:54 Windows%2010%20AP-GS.ova)111/tcp: RPC에 의한 시스템 정보 노출 가능성 존재139/tcp, 445/tcp: Samba 기반의 공유폴더 서비스3389/tcp: XRDP 기반의 원격접속 서비스 (윈도우의mstsc.exe, 칼리의rdesktop으로 접속하여 확인 가능)8200/tcp: MiniDLNA 1.2.1 (OS: Debian; DLNADOC 1.50; UPnP 1.0) - OS 정보 노출9091/tcp: 트랜스미션 포트(Transmission BitTorrent management httpd)39507/tcp: RPC 관련 포트?43389/tcp: SSL 기반의 데스크톱 접속 서비스? (윈도우의 원격접속 서비스로 추정:mstsc.exe로 접속하여 확인 가능51413/tcp: Kerberos 관련 포트?참고: 이 포트들은 모두 외부 접속을 차단하는 것으로 보고서를 작성하고 취약점 점검에서는 제외하여 진행; 반면, 해커라면 모든 포트에 대한 공격을 진행할 것임- 서버 정보를 제공하는 HTTP 헤더 (탐지도구: nmap, nikto)
http-server-header: Apache/2.4.41 (Win64) PHP/7.4.2: 윈도우 기반 PHP 서비스- 불필요한 HTTP 메소드 활성화
TRACE(탐지도구: nikto)
kali@kali:~$ curl -X TRACE http://172.16.15.116:40080 --header "XXX: 서버 응답으로 반환시 XST 위험성 존재" TRACE / HTTP/1.1 Host: 172.16.15.116:40080 User-Agent: curl/7.64.0 Accept: */* XXX: 서버 응답으로 반환시 XST 위험성 존재 kali@kali:~$
TRACE 메소드는 이론적으로 XST(Cross-site Tracing) 공격의 대상이 될 수 있으나 2020년 5월 현재, TRACE를 강제화 할 수 있는 웹 브라우저나 언어가 없어서 위험하지는 않음- 불필요한 파일/페이지
:40080/test.php:phpinfo()결과에서 상세한 시스템 정보 노출 (탐지도구: nikto):40080/readme.txt: 공개용 소프트웨어인GetSimple CMS의 기본 소개문서 (탐지도구: nikto)
공개용 취약점 점검 도구의 스캔 결과 요약
kali@kali:~$ curl http://172.16.15.116:40080/data/users/ <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN"> <html> <head> <title>Index of /data/users</title> </head> <body> <h1>Index of /data/users</h1> <ul><li><a href="/data/"> Parent Directory</a></li> <li><a href="admin%20-%20%eb%b3%b5%ec%82%ac%eb%b3%b8.xml"> admin - 복사본.xml</a></li> <li><a href="admin.xml"> admin.xml</a></li> </ul> </body></html> kali@kali:~$ curl http://172.16.15.116:40080/data/users/admin.xml <?xml version="1.0" encoding="UTF-8"?> <item><USR>admin</USR><NAME>관리자</NAME><PWD>264bc0768362a68984faea923efaa21f67f4d10a</PWD><EMAIL>admin@test.com</EMAIL><HTMLEDITOR>1</HTMLEDITOR><TIMEZONE>Asia/Seoul</TIMEZONE><LANG>en_US</LANG></item> kali@kali:~$
이제는 :40080/admin/의 관리자 로그인 기능, 위의 관리자 계정정보 등을 이용하여
원래는 노출되지 않아야 할 관리기능에 접근하여 추가적인 취약점을 점검하는 것으로
수동점검이 진행된다.
관리자의 글쓰기 기능, 첨부파일 또는 파일업로드 기능, 게시판에 의한 XSS 취약점 등이
주요 점검대상이 된다.
공개용 CMS를 사용하고 있으므로 점검자는 직접 GetSimple을 설치하여
GetSimple 자체의 취약점을 찾아볼 수도 있을 것이다.
(참고: 40080 포트의 서비스는 관리자 계정 유추로 인하여 시스템 장악이 가능하다.)
이 훈련장은 MS Windows 기반의 훈련장이므로 불특정 다수에게 배포할 수 없다. 경험을 원하는 경우에는 아래에 적힌 메일로 요청해주시길.
GetSimple은 실제로 다수의 누리집에서 사용하는 PHP 기반의 공개용 CMS이다.
이 훈련장은 인터넷에서 찾을 수 있는 설치 방법대로 Apache2, PHP, GetSimple을 설치한 상태이다.
보안에 신경쓰지 않을 경우에 어떤 위험성이 발생할 수 있는 지는 인터넷에서도 직접 확인할 수 있다.
Google 검색 엔진에서 title:"index of" /data/users xml 검색결과를 보면
확인할 수 있다.
구글링 결과 확인해 보기
[처음 작성한 날: 2020.05.07] [마지막으로 고친 날: 2020.05.09]
> 다음 글 : Kali Linux 2020.1b 64bit 설치 설명서 (MS 윈도우 10, VMware 플레이어) (2020.03.25)
 이 저작물은 크리에이티브
커먼즈 저작자표시 4.0 국제 라이선스에 따라 이용할 수 있습니다.
이 저작물은 크리에이티브
커먼즈 저작자표시 4.0 국제 라이선스에 따라 이용할 수 있습니다.
잘못된 내용, 오탈자 및 기타 문의사항은 j1n5uk{at}daum.net으로 연락주시기 바랍니다.
문서의 시작으로 컴퓨터 깨알지식 웹핵 누리집 대문