>> 목록보이기
#웹취약점 분석도구
#nikto
#owasp-zap
#취약점 분석 뜯어보기
nikto와 owasp-zap을 연동하여 취약점 탐색하기
웹핵누리집에서 가장 많이 언급될 웹취약점점검 도구가 nikto와 owasp-zap이다.
이 둘은 대부분 독립적으로 사용하지만 서로 연동시켜서 사용할 수도 있다.
연동법은 아래와 같다.
nikto -host www.target.site -useproxy http://localhost:8080/
즉 nikto의 HTTP 프록시로 owasp-zap을 연결시키는 것이다.
이렇게 하면 nikto가 owasp-zap에 nitko가 접속한 HTTP 통신이 모두 저장된다.
이를 살펴보면 nikto가 어떤 방식으로 취약점을 탐지하는 지 알아볼 수 있다.
root@kali:~# owasp-zap 2&> /dev/null & [1] 14417 root@kali:~# nikto -host webhack.dynu.net -useproxy http://localhost:8080 - Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: (proxied) + Target Hostname: webhack.dynu.net + Target Port: 80 + Proxy: localhost:8080 + Start Time: 2016-12-04 23:27:29 (GMT9) --------------------------------------------------------------------------- + Server: Apache + No CGI Directories found (use '-C all' to force check all possible dirs) + Server leaks inodes via ETags, header found with file /robots.txt, fields: 0x24 0x5411937436827 + "robots.txt" contains 1 entry which should be manually viewed. + Web Server returns a valid response with junk HTTP methods, this may cause false positives. + DEBUG HTTP verb may show server debugging information. See http://msdn.microsoft.com/en-us/library/e8z01xdh%28VS.80%29.aspx for details. + OSVDB-3233: /icons/README: Apache default file found. + 7512 requests: 28 error(s) and 5 item(s) reported on remote host + End Time: 2016-12-05 00:57:34 (GMT9) (5405 seconds) --------------------------------------------------------------------------- + 1 host(s) tested root@kali:~#
위는 웹핵누리집(webhack.dynu.net)을 대상으로 nikto를 실행한 사례이다.
먼저 owasp-zap을 실행하였다.
이때 owasp-zap은 8080 포트에서 HTTP 프록시 기능을 수행한다.
nikto 실행 시에는 -useproxy를 이용하여 ZAP의 프록시 서버와 연결할 수 있다.
nikto가 취약점점검을 진행하는 동안 owasp-zap은 닉토의 요청과 웹핵 서버의
응답을 모두 저장한다.
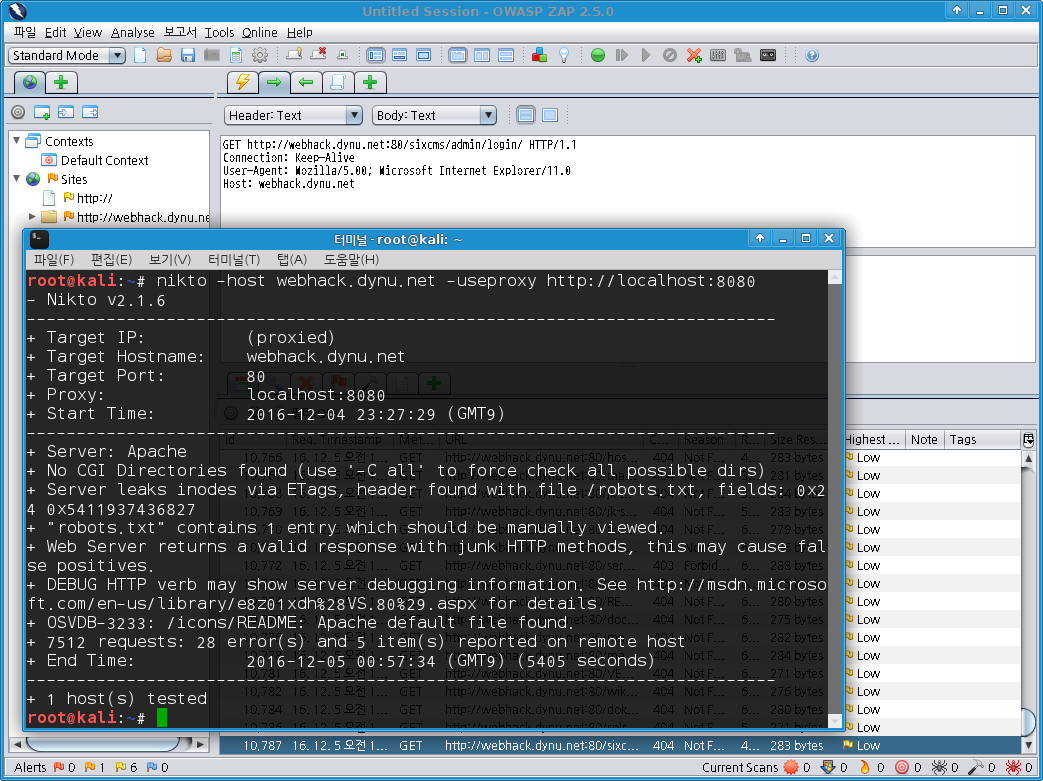
[ ↑ nikto와 owasp-zap을 연동시켜서 nikto 실행을 완료한 모습 ]
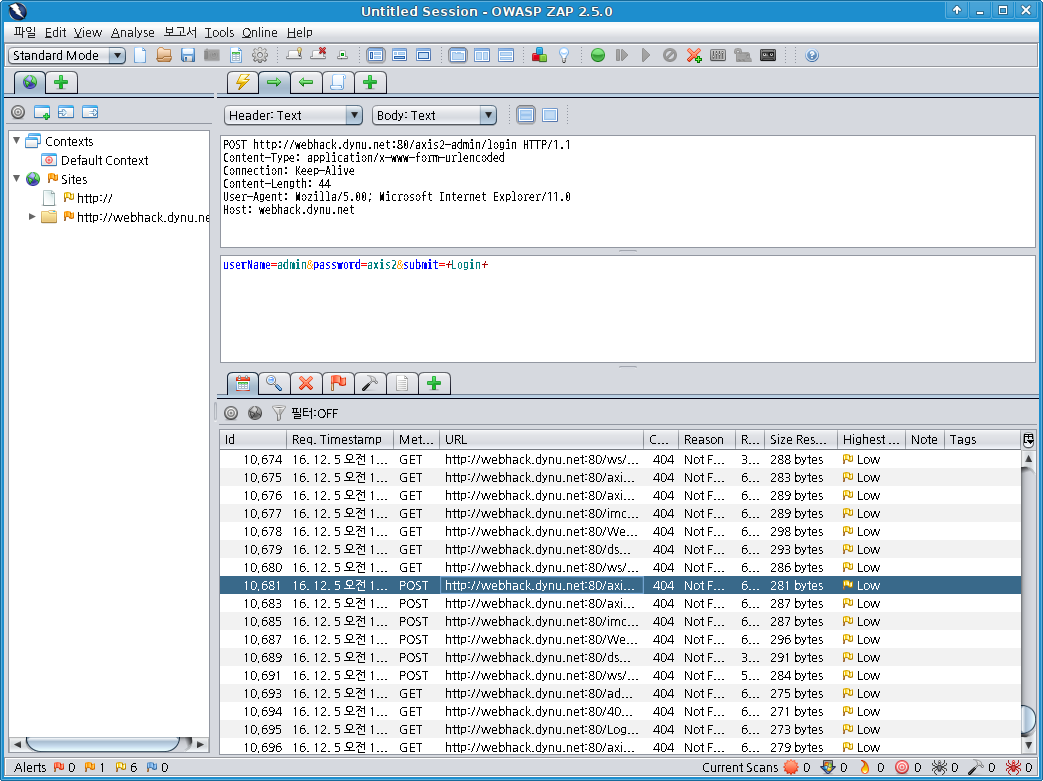
[ ↑ owasp-zap에서 nikto의 점검 방법 확인 가능: axis2 점검 사례 ]
위의 그림은 nikto가 webhack.dynu.net에 Axis2 관리자 페이지가 존재하는 지와 존재한다면
초기관리자 비번을 사용하는 지를 탐색한 HTTP 통신이다.
HTTP 요청은 다음과 같다.
POST http://webhack.dynu.net:80/axis2-admin/login HTTP/1.1 Content-Type: application/x-www-form-urlencoded Connection: Keep-Alive Content-Length: 44 User-Agent: Mozilla/5.00; Microsoft Internet Explorer/11.0 Host: webhack.dynu.net userName=admin&password=axis2&submit=+Login+
Apache Axis2는 아파치 재단이 배포하는 Web 서비스 / SOAP / WSDL 엔진이다.
관리자 페이지의 초기 ID/PW가 "admin/axis2"이다.
위의 Apache Axis2의 사례처럼 nikto가 실제 점검에서 사용하는 HTTP 통신을 관찰해보면
입문자에게는 좋은 학습재료가 된다.
또는 칼리리눅스에서 nikto의 취약점 데이터베이스는 /usr/share/nikto/databases/에 위치한다.
root@kali:~# ls /usr/share/nikto/databases/ 합계 1600 4 db_404_strings 4 db_embedded 4 db_multiple_index 36 db_server_msgs 4 db_content_search 12 db_favicon 132 db_outdated 8 db_subdomains 16 db_dictionary 4 db_headers 4 db_parked_strings 1208 db_tests 144 db_drupal 4 db_httpoptions 12 db_realms 4 db_variables root@kali:~# grep -i axis2 /usr/share/nikto/databases/db_* /usr/share/nikto/databases/db_tests:"001374","4808","70","/axis-cgi/buffer/command.cgi","GET","200","","","","","Axis WebCam 2400 may allow overwriting or creating files on the system. See http://www.websec.org/adv/axis2400.txt.html for details.","","" /usr/share/nikto/databases/db_tests:"001375","4806","3","/support/messages","GET","200","","","","","Axis WebCam allows retrieval of messages file (/var/log/messages). See http://www.websec.org/adv/axis2400.txt.html","","" /usr/share/nikto/databases/db_tests:"006479","0","3","@AXIS2axis2-web/HappyAxis.jsp","GET","Axis2\sHappiness\sPage","Back\sHome","","","","Apache Axis2 Happiness Page identified which includes internal application details.","","" /usr/share/nikto/databases/db_tests:"006486","59001","7","@AXIS2services/Version?xsd=../../../../../../../../../../../etc/passwd","GET","root:","","","","","Apache Axis2 contains a directory traversal in the Version program.","","" /usr/share/nikto/databases/db_tests:"006707","0","be","@AXIS2axis2-admin/","GET","Axis2\sadministration\sconsole","","","","","Apache Axis2 administration console found.","","" /usr/share/nikto/databases/db_tests:"006990","0","3b","@AXIS2services/Version/getVersion","GET","Hello\sI\sam\sAxis2","Hi\s-\sthe\sAxis2\sversion\sis","","","","Apache Axis2 version identified.","","" /usr/share/nikto/databases/db_tests:"007000","0","d","@AXIS2services/listServices","GET","<title>List\sServices","","","","","Apache Axis2 WebServices identified.","","" /usr/share/nikto/databases/db_tests:"007001","0","b","@AXIS2axis2-web/index.jsp","GET","<title>Axis\s2\s-\sHome","","","","","Apache Axis2 Web Application identified.","","" /usr/share/nikto/databases/db_tests:"007004","68662","b8e","@AXIS2axis2-admin/login","POST","Welcome\sto\sAxis2\sWeb\sAdmin\sModule\s!!","","","","","Apache Axis2 administration console with default credentials admin:axis2 found (CVE-2010-2103), see also http://www.rapid7.com/security-center/advisories/R7-0037.jsp","userName=admin&password=axis2&submit=+Login+","" /usr/share/nikto/databases/db_tests:"007009","0","be","@AXIS2Login.jsp","GET","Login\sto\sAxis2::","","","","","Apache Axis2 administration console found.","","" /usr/share/nikto/databases/db_variables:@AXIS2=/ /axis2/ /imcws/ /WebServiceImpl/ /dswsbobje/ /ws/ root@kali:~#
/usr/share/nikto/databases/db_tests 파일에 Apache Axis2의 기본 관리자 정보(admin:axis2) 점검 항목을
찾을 수 있다.
이외에도 Axis2에는 경로조작(Path Traversal) 취약점도 존재하는 것을 알 수 있다.
grep -i tomcat /usr/share/nikto/databases/db_*
Apache Tomcat 점검 항목과 취약점에 대한 단서를 볼 수 있을 것이다.
[처음 작성한 날: 2016.12.06] [마지막으로 고친 날: 2016.12.06]
< 이전 글 : 오늘의 웹서버 공격 로그, XML-RPC, Open Proxy (2016.12.08)
> 다음 글 : 미라이 IoT DDoS 봇넷이 사용한 61개 비밀번호 (2016.12.05)
 이 저작물은 크리에이티브
커먼즈 저작자표시 4.0 국제 라이선스에 따라 이용할 수 있습니다.
이 저작물은 크리에이티브
커먼즈 저작자표시 4.0 국제 라이선스에 따라 이용할 수 있습니다.
잘못된 내용, 오탈자 및 기타 문의사항은 j1n5uk{at}daum.net으로 연락주시기 바랍니다.
문서의 시작으로 컴퓨터 깨알지식 웹핵 누리집 대문